
Communication
Investment
Platform
Security
Miscellaneous
Reviews
Compare the wallets
Top WalletsTrezor
Trezor Safe 5BlockStream
BlockStream JadeLedger
Ledger Nano XSafePal
SafePal S1 ProEllipal
Ellipal Titan 2
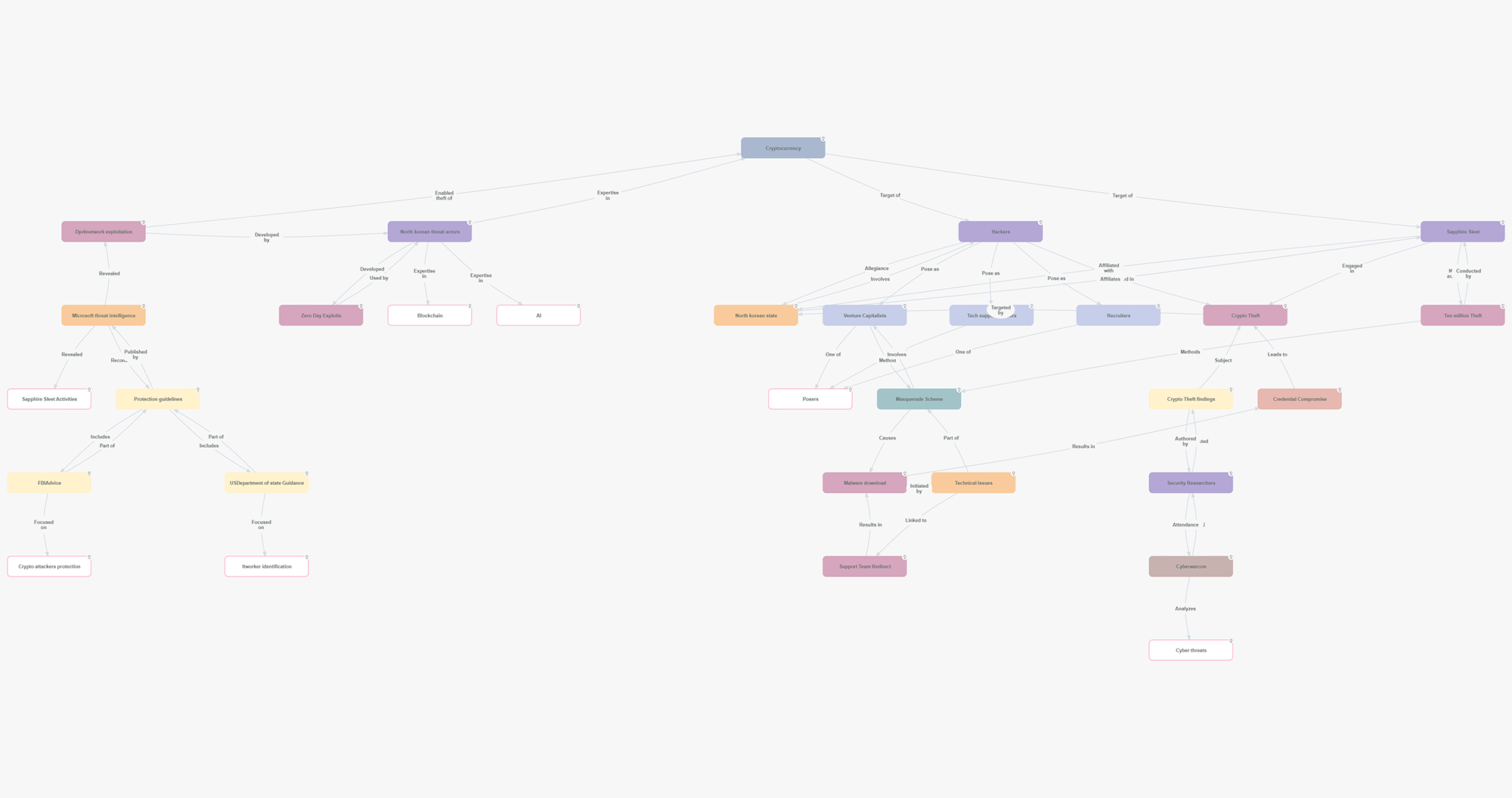
North Korean state-sponsored hackers, notably the Lazarus Group, have become infamous for their relentless cyberattacks targeting financial systems and cryptocurrency markets. These sophisticated operations, such as the "Sapphire Sleet" campaign, exploit blockchain vulnerabilities, employ advanced tactics like zero-day exploits, and leverage masquerade schemes to steal millions in digital assets. As cryptocurrency gains prominence, these threats expose critical gaps in security infrastructure, emphasizing the need for collective defense strategies. This article explores the intricate web of North Korean cybercrime, its implications for investors and the global economy, and the crucial steps necessary to safeguard digital assets from these persistent adversaries.
North Korea's state-sponsored hacking groups, including the infamous Lazarus Group, are orchestrating sophisticated cyberattacks like "Sapphire Sleet" to steal cryptocurrency and exploit blockchain vulnerabilities. Their advanced tactics, including masquerade schemes and zero-day exploits, have led to multi-million dollar thefts, challenging global cybersecurity defenses. Collaborative efforts and innovations like AI and blockchain are crucial to counter these persistent threats. Learn more about their operations and defense strategies.

North Korea’s cybercrime activities have escalated over the past decade, with sophisticated attacks targeting financial systems and cryptocurrency markets. In 2023, the "Sapphire Sleet" operation emerged, focusing on blockchain exploitation and crypto theft. High-profile heists, such as a $10 million cryptocurrency theft, underline the increasing complexity and scope of these operations.
This article delves into the escalating cyber threats posed by North Korea’s state-sponsored hacking groups, including the infamous Lazarus Group and their "Sapphire Sleet" operations. These hackers employ advanced techniques such as masquerade schemes and zero-day exploits to infiltrate cryptocurrency systems, resulting in multi-million dollar thefts. Recent cases highlight the vulnerabilities of blockchain technologies and the critical need for robust cybersecurity measures. Collaborative efforts among tech workers, recruiters, researchers, and government agencies have proven pivotal in countering these threats. The article underscores the vital role of blockchain and AI in fortifying defenses, as well as the significance of collective global efforts to mitigate the risks associated with cybercrime.
| Entity | Related Search Terms |
|---|---|
| North Korean hackers | Lazarus Group, Sapphire Sleet |
| Crypto theft | Blockchain vulnerabilities, AI in cybersecurity |
| Sapphire Sleet | North Korea, cybercrime operations |
| Lazarus Group | North Korean state hackers |
| Microsoft Threat Intelligence | Cybersecurity, DPRK network exploitation |
| Bankman-Fried | FTX scandal, Insiders Avoidance Complaint |
| FTX Trading Ltd. | Alameda Research, crypto lawsuits |
| FBI | Cybercrime investigation, sanctions |
| Cyberwarcon | Cybersecurity conference, global collaboration |
Using a secure hardware wallet is one of the best ways to protect your cryptocurrency assets against cyber theft. Hardware wallets ensure private keys are stored offline, beyond the reach of hackers exploiting blockchain vulnerabilities.
Preventative Steps:
By integrating these tools and strategies, users and organizations can mitigate risks and enhance overall cybersecurity.