
Communication
Investment
Platform
Security
Miscellaneous
Reviews
Compare the wallets
Top WalletsTrezor
Trezor Safe 5BlockStream
BlockStream JadeLedger
Ledger Nano XSafePal
SafePal S1 ProEllipal
Ellipal Titan 2
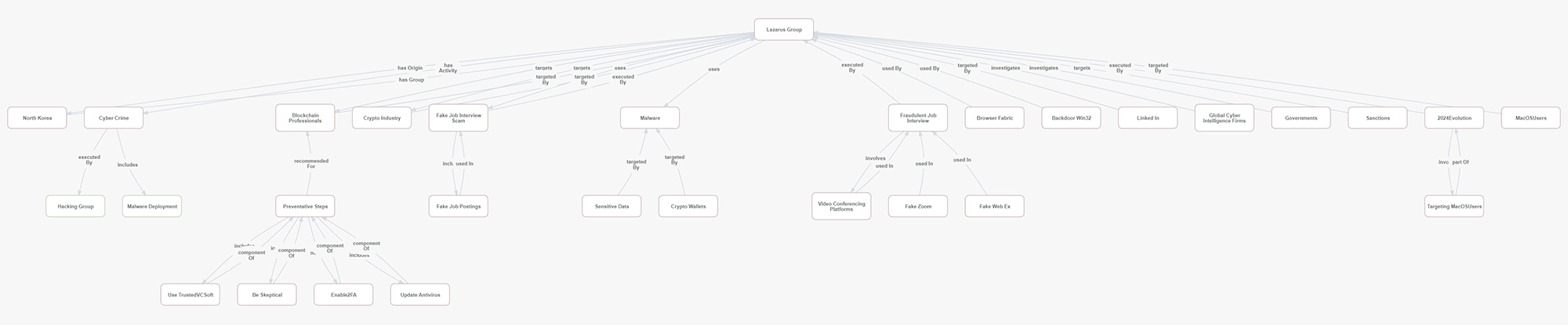
The Lazarus Group, a North Korean hacking collective, has evolved its tactics to exploit professionals in the cryptocurrency and blockchain sectors. By using fraudulent job offers posted on platforms like LinkedIn, the group lures victims into fake video conferencing interviews. During these interactions, malware such as BrowserFabric and Backdoor.Win32 is deployed, enabling the hackers to steal sensitive data, including access to cryptocurrency wallets and personal information. The Lazarus Group's strategy specifically targets high-value individuals and organizations in the blockchain industry, putting investors and professionals at serious risk of financial loss and security breaches.
The Lazarus Group, a North Korean hacking collective, is targeting blockchain professionals with fake job interview invitations, primarily distributed via LinkedIn and video conferencing platforms. These scams install malware like BrowserFabric and Backdoor.Win32, aimed at stealing cryptocurrency and sensitive data. MacOS users, particularly those in blockchain, are now key targets. Stay vigilant against unsolicited job offers, especially those requiring the use of unfamiliar conferencing software. Learn more about how this scam works and how to protect your crypto assets.

The Lazarus Group, a notorious North Korean hacking group, has evolved its tactics to target professionals in the blockchain and cryptocurrency industries through fake job interview scams. Using platforms like LinkedIn and sophisticated malware such as BrowserFabric and Backdoor.Win32, the group lures victims into fake video interviews, where they exploit video conferencing software to install malware. This malware grants Lazarus access to sensitive data, including cryptocurrency wallets and personal identification information. Their targets range from blockchain developers to crypto exchange employees, with recent campaigns focusing on MacOS users, making their attacks more versatile and potent.
The Lazarus Group's operations are internationally condemned, with governments and cybersecurity firms closely monitoring their activities. While no specific monetary loss has been disclosed, the methods of attack are primarily focused on stealing cryptocurrency and proprietary blockchain technologies.
Governments and legal bodies are stepping up their measures against the Lazarus Group, which has been involved in major cyber thefts globally. Security experts are warning individuals in the blockchain space to be cautious when engaging with unsolicited job offers, particularly those involving video conferencing software.
| Entity | Related Search Terms |
|---|---|
| Lazarus Group | North Korean hackers, Lazarus hacking group |
| BrowserFabric | BrowserFabric malware, video conferencing malware |
| Backdoor.Win32 | Backdoor malware, Win32 exploit |
| Blockchain professionals | Blockchain job scam, crypto job interview scams |
| MacOS | MacOS malware, North Korean MacOS hacks |
| Cryptocurrency wallets | Crypto theft, wallet hacks, cryptocurrency hacks |
| LinkedIn job scam, Lazarus job ads |
How Hardware Wallets Could Help: Using hardware wallets would add a layer of security for victims, as these wallets are offline and immune to malware infections caused by phishing or malicious video conferencing software.
Additional Preventative Steps: